Table of Contents
Web
Browser
Your browser is the first exposed.
- add DuckDuckGo HTML and/or Startpage to your list of search engines;
- Extensions:
- configurations in about:config with the file
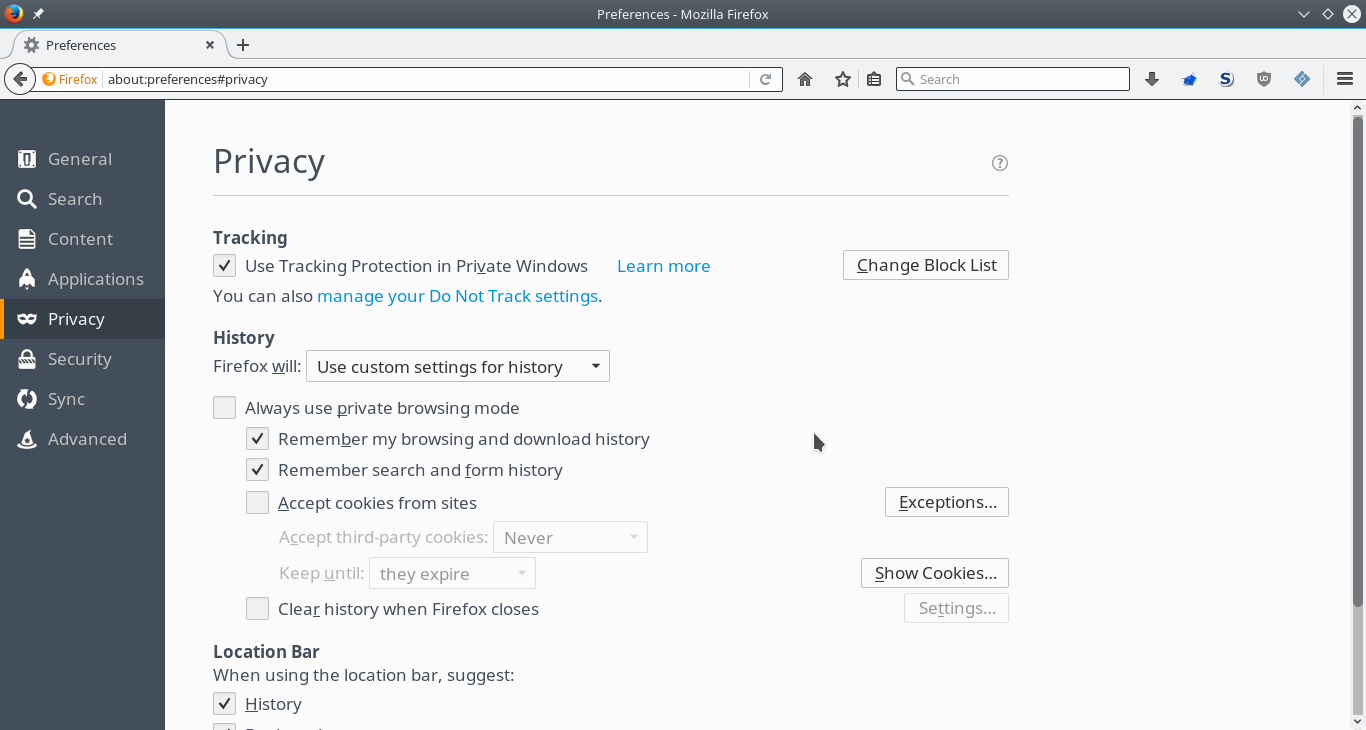
user.js: - Firefox preferences:
- in the privacy tab precise that you do not want to be tracked by sites;
- do not accept cookies from sites and allow (for session only) sites you trust ( example);
- install Tor/Privoxy and use FoxyProxy to switch faster between Tor and the “no proxy” mode;
- do not use Tor without HTTPS on sensible sites;
- avoid using Google DNS (even if they are fast and reliable). Prefer French Data Network DNS resolvers (80.67.169.12, 80.67.169.40).
Another good solution is to use the Tor Browser which is based on Firefox and pre-configured with the best settings for your privacy and uses the Tor network by default. No technical knowledge is required.
If you are using a public computer I recommend you Tails.
Firefox preferences
User preferences
<html><script src=“https://gist.github.com/cedricbonhomme/de05a2413273b8a3b7de.js”></script></html>
Privacy
Browsing advices
- check for the “lock” icon on the status bar (depends on the browser) that shows that you are on a secured web site. Also check that the URL begins with “https” in the location bar when making transactions online;
- always check the URL before clicking on a link;
- phishing:
- use the navigation bar history to prevent malicious URL;
- check that your browser is able to automatically fill in login forms with your information;
Social networking
- limit the usage of social networking services;
- check your public identity, for example by searching your name in Google (you can use Google Alerts or a script you wrote);
- disable Google search history and Google location history;
- when possible, use two-factor authentication (possible with Google and Github for instance);
- do not log into private services on public computers;
- do not hook all your online services together;
- do not share your phone's location data;
- do not upload geotagged photos in the region your living (check the configuration of your smartphone and/or tablet);
- do not allow people to tag your face;
- do not share your Likes, +1s or whish lists. Prefer the use of bookmarks;
- ensure that after a POP the fetched messages have been removed from the server;
- when possible uses GnuPG to encrypt (and sign) your emails;
- consider the use of alternatives like Bitmessage;
Instant messaging
Alternatives to well known spied systems:
- DukGo or another Jabber/XMPP service. Use Off-the-Record (OTR), easy with Pidgin or Kopete;
- a worth watching project: TIMB;
- another interesting project: Ricochet;
- IRC.
System
/etc/hosts
The content of my /etc/hosts file is based on this very good example.
DNS
Choose the Domain Name Server you want to use.
Solution 1
Probably the best solution. Lets you add your DNS servers with a higher priority than the DNS servers provided by the DHCP.
resolvconf is a set of scripts and hooks managing DNS resolution.
The configuration of the internet connection is specified in the file /etc/resolvconf. It is possible to edit this file, but any change manually done will be lost as it gets overwritten next time something triggers resolvconf.
A solution is to use the file /etc/resolvconf/resolv.conf.d/head in order to ensure a DNS server is always the first one in the list.
# apt-get install resolvconf # cat /etc/resolvconf/resolv.conf.d/head # Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8) # DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN # French Data Network DNS resolvers nameserver 80.67.169.12 nameserver 80.67.169.40 # resolvconf -u
Solution 2
If your interface is configured statically then you can change your DNS by this manner:
# vim /etc/network/interfaces
Add this section:
iface eth0 inet static address 192.168.1.11 netmask 255.255.255.0 gateway 192.168.1.1 dns-nameservers 80.67.169.12 80.67.169.40
Restart the interface and check:
# ifdown eth0 # ifup eth0 # exit $ nslookup cedricbonhomme.org Server: 80.67.169.40 Address: 80.67.169.40#53
An alternative is to use the NetworkManager.
Services providers
- bring a special care to the choice of service providers you use. For example if your country is under surveillance (like France), avoid as much as possible services from this country (Orange, SFR, etc.). A good idea is to configure Tor in order to never use an exit node in this country;